Would you like to attend Cisco 210-060 latest dumps? The Implementing Cisco Collaboration Devices v1.0 (210-060 CICD) exam is a 75 Minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCNA Collaboration certification. High quality Cisco 210-060 dumps CICD exam video Cisco Certified Network Associate Collaboration Certification Core Subjects to Be Certified guaranteed success. “Implementing Cisco Collaboration Devices v1.0” is the exam name of Pass4itsure Cisco 210-060 dumps test which designed to help candidates prepare for and pass the Cisco 210-060 exam. Keeping the in mind, the examiner has bouncily declared the prerequisite of the https://www.pass4itsure.com/210-060.html dumps Cisco Certified Network Associate Collaboration. To earn Implementing Cisco Collaboration Devices, it’s essential for each individual to have current and valid Cisco Certified Network Associate Collaboration.
[Cisco Data Center Cisco 210-060 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNmlXYjFDT0t3UWc
[Microsoft Data Center Microsoft 070-461 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWRFNLVl8xNFJPejg
Pass4itsure Cisco 210-060 Dumps Exam Questions – 100% Success Guaranteed:
QUESTION 120
Use the router console to view the configuration and answer the question.
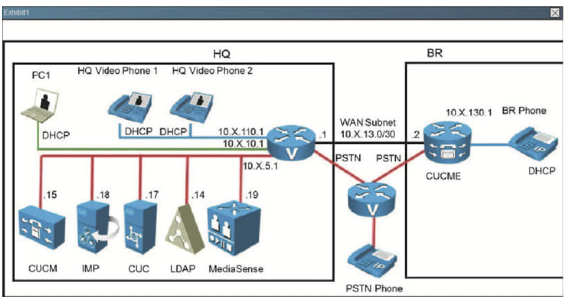
When a call is placed from the Branch Router phone to the PSTN number of 914085551212, the call is failing. What dial peer is supposed to be used and why is the call failing? Select 2 (two)
A. dial-peer voice 910 pots
B. dial-peer voice 9 pots
C. dial-peer voice 9001 voip
D. destination pattern is incorrect
E. prefix is missing from the dial-peer
F. the port assignment is incorrect in the dial-peer
G. the port number is missing in the dial-peer
210-060 exam Correct Answer: BF
QUESTION 121
Which four fields must an administrator complete to create a new user in Cisco Unity Connection? (Choose four.)
A. Alias
B. User type
C. Extension
D. Corporate email address
E. First name
F. Last name
G. Employee ID
H. Template
Correct Answer: ABCH
QUESTION 122
A user would like all calls to be forwarded to voice mail. The user\’s phone is not set up with a soft key for this feature. Which option accomplishes this configuration from within the Cisco Unified Communication Administrator Directory Number configuration page?
A. Call Forward and Pickup Settings andgt; Forward No Coverage External andgt; Select voice mail check box
B. Call Forward and Pickup Settings andgt; Forward Busy External andgt; Select voice mail check box
C. Call Forward and Pickup Settings andgt; Forward All andgt; Select voice mail check box
D. Call Forward and Pickup Settings andgt; Forward Unregistered External andgt; Select voice mail check box
210-060 dumps Correct Answer: C
QUESTION 123
Which four tasks does RTMT allow an administrator to perform? (Choose four.)
A. View syslog messages.
B. Generate alerts when threshold is below or above user-configured.
C. Monitor a set of predefined management objects that monitor the health of the system.
D. Collect information and traces about errors or alerts that exist in the RTMT.
E. Reboot the system.
F. Perform incremental backups.
G. Export CDR.
Correct Answer: ABCD
QUESTION 124
Which three features of the Cisco Unified Attendant Console can a user use to streamline the company telephony communications? (Choose three.)
A. promotes a phone call into a video call
B. uses presence status to determine availability
C. reverts back to operator a transferred call
D. provides a conference call with up to 10 participants
E. provides call detail records reports to upper management
F. defines operator working hours and automatically redirect calls
210-060 exam Correct Answer: BCF
QUESTION 125
In which section of Cisco Unified Communications Manager are Call Detail Records viewed?
A. Cisco Unified Serviceability
B. Cisco Unified OS Administration
C. Cisco Unified Reporting
D. Cisco Unified Communications Manager Administration
E. Cisco Unified Disaster Recovery
Correct Answer: A
QUESTION 126
Customer requirements dictate that local calls from area code 408 display the ANI as a 7-digit number. Which procedure allows the leading digits to be stripped as soon as they arrive at the H.323 voice gateway?
A. Set up a voice translation rule, apply the translation rule to a translation profile, and apply the translation profile to the dial peer in the inbound direction.
B. Set up a voice translation profile, apply the translation profile to a translation rule, and apply the translation rule to the dial peer in the outbound direction.
C. Set up a voice translation rule, apply the translation rule to a translation profile, and apply the translation profile to the dial peer in the outbound direction.
D. Set up a voice translation profile, apply the translation profile to a translation rule, and apply the translation rule to the dial peer in the inbound direction.
210-060 dumps Correct Answer: A
QUESTION 127
Which command allows the telephony service of a Cisco Unified Communications Manager Express router to be associated to loopback address 192.168.143.44?
A. ! telephony-service max-ephones 4 max-dn 8 ip source-address 192.168.143.44 !
B. ! telephony-service max-ephones 4 max-dn 8 ip bind src-addr 192.168.143.44 !
C. ! telephony-service max-ephones 4 max-dn 8 source-address ipv4:192.168.143.44 !
D. ! telephony-service max-ephones 4 max-dn 8 ip address 192.168.143.44 !
Correct Answer: A
QUESTION 128
Which option allows an engineer to deploy new firmware to a single phone, while reducing possible impact?
A. Define a new firmware load on specific device. Save configuration and reset individual device.
B. Define load in device defaults. Reset Device Pool.
C. Upload firmware to TFTP server. Restart TFTP service.
D. Enable Peer Firmware Sharing.
210-060 pdf Correct Answer: A
QUESTION 129
The receptionist has a Cisco 7965 phone with 24-button side-car configuration. The side-car button of the phone does
not light up when the line is in use. Which phone configuration is missing?
A. Subscriber calling search space
B. Location
C. BLF audible alert setting
D. Phone button template
Correct Answer: A
QUESTION 130
Which three methods can an engineer use to create users in Cisco Unity Connection? (Choose three.)
A. Local
B. Cisco Unified Presence Server
C. Cisco Unified Communications Manager
D. LDAP
E. TMS
F. Outlook
210-060 vce Correct Answer: ACD
QUESTION 131
Which Cisco Unified Communications Manager device report provides key information to determine if an additional gateway is needed?
A. Gateway utilization
B. Gateway summary
C. Gateway detail
D. Gateway and line group utilization
Correct Answer: A
QUESTION 132
What is one advantage of importing Cisco Unity Connection users from Cisco Unified Communications Manager?
A. The extension can be manually changed.
B. The extension stays synchronized with the user extension.
C. Voicemail features can be administered.
D. Voicemail does not require an additional license.
210-060 exam Correct Answer: B
QUESTION NO: 133
Which of the following sections come under the ISO/IEC 27002 standard?
A. Security policy
B. Asset management
C. Financial assessment
D. Risk assessment
Answer: A,B,D
Explanation: ISO/IEC 27002 is an information security standard published by the International Organization for Standardization (ISO) and by the International Electrotechnical Commission (IEC) as ISO/IEC 17799:2005. This standard contains the following twelve main sections:
1.Risk assessment: It refers to assessment of risk.
2.Security policy: It deals with the security management.
3.Organization of information security: It deals with governance of information security.
4.Asset management: It refers to inventory and classification of information assets.
5.Human resources security: It deals with security aspects for employees joining, moving and leaving an organization.
6.Physical and environmental security: It is related to protection of the computer facilities.
7.Communications and operations management: It is the management of technical security controls in systems and networks.
8.Access control: It deals with the restriction of access rights to networks, systems, applications, functions and data.
9.Information systems acquisition, development and maintenance: It refers to build security into applications.
10.Information security incident management: It refers to anticipate and respond appropriately to information security breaches. 11.Business continuity management: It deals with protecting, maintaining and recovering business-critical processes and systems. 12.Compliance: It is used for ensuring conformance with information security policies, standards, laws and regulations.
Answer: C is incorrect. Financial assessment does not come under the ISO/IEC 27002 standard.
QUESTION NO: 134
Which of the following statements about the authentication concept of information security management is true?
A. It establishes the users’ identity and ensures that the users are who they say they are.
B. It ensures the reliable and timely access to resources.
C. It determines the actions and behaviors of a single individual within a system, and identifies that particular individual.
D. It ensures that modifications are not made to data by unauthorized personnel or processes.
210-060 dumps Answer: A
Explanation: The concept of authentication establishes the users’ identity and ensures that the users are who they say they are. Answer: B is incorrect. The concept of availability ensures the reliable and timely access to data or resources. Answer: D is incorrect. The concept of integrity ensures that modifications are not made to data by unauthorized personnel or processes. Answer: C is incorrect. The concept of accountability determines the actions and behaviors of a single individual within a system, and identifies that particular individual.
QUESTION NO: 135
Billy is the project manager of the HAR Project and is in month six of the project. The project is scheduled to last for 18 months. Management asks Billy how often the project team is participating in risk reassessment in this project. What should Billy tell management if he’s following the best practices for risk management?
A. Project risk management happens at every milestone.
B. Project risk management has been concluded with the project planning.
C. Project risk management is scheduled for every month in the 18-month project.
D. At every status meeting the project team project risk management is an agenda item.
Answer: D
Explanation:
Risk management is an ongoing project activity. It should be an agenda item at every project status meeting. Answer: A is incorrect. Milestones are good times to do reviews, but risk management should happen frequently. Answer: C is incorrect. This answer would only be correct if the project has a status meeting just once per month in the project. Answer: B is incorrect. Risk management happens throughout the project as does project planning.
QUESTION NO: 136
You work as a security manager for BlueWell Inc. You are going through the NIST SP 800-37 C&A methodology, which is based on four well defined phases. In which of the following phases of NIST SP 800-37 C&A methodology does the security categorization occur?
A. Security Accreditation
B. Security Certification
C. Continuous Monitoring
D. Initiation
210-060 pdf Answer: D
Explanation: The various phases of NIST SP 800-37 C&A are as follows: Phase 1: Initiation- This phase includes preparation, notification and resource identification. It performs the security plan analysis, update, and acceptance. Phase 2: Security Certification- The Security certification phase evaluates the controls and documentation. Phase 3: Security Accreditation- The security accreditation phase examines the residual risk for acceptability, and prepares the final security accreditation package. Phase 4: Continuous Monitoring-This phase monitors the configuration management and control, ongoing security control verification, and status reporting and documentation.
QUESTION NO: 137
In which of the following DIACAP phases is residual risk analyzed?
A. Phase 1
B. Phase 5
C. Phase 2
D. Phase 4
E. Phase 3
Answer: D
Explanation: The Department of Defense Information Assurance Certification and Accreditation Process (DIACAP) is a process defined by the United States Department of Defense (DoD) for managing risk. The Certification Determination and Accreditation phase is the third phase in the DIACAP process. Its subordinate tasks are as follows: Analyze residual risk. Issue certification determination. Make accreditation decision. Answer: A is incorrect. Phase 1 is known as Initiate and Plan IA C&A. Answer: C is incorrect. Phase 2 is used to implement and validate assigned IA controls. Answer: E is incorrect. Phase 3 is used to make certification determination and accreditation decisions. Answer: B is incorrect. Phase 5 is known as decommission system and is used to conduct activities related to the disposition of the system data and objects.
QUESTION NO: 138
Which of the following security controls will you use for the deployment phase of the SDLC to build secure software? Each correct answer represents a complete solution. Choose all that apply.
A. Change and Configuration Control
B. Security Certification and Accreditation (C&A)
C. Vulnerability Assessment and Penetration Testing
D. Risk Adjustments
210-060 vce Answer: B,C,D
Explanation: The various security controls in the SDLC deployment phase are as follows: Secure Installation: While performing any software installation, it should kept in mind that the security configuration of the environment should never be reduced. If it is reduced then security issues and overall risks can affect the environment. Vulnerability Assessment and Penetration Testing: Vulnerability assessments (VA) and penetration testing (PT) is used to determine the risk and attest to the strength of the software after it has been deployed. Security Certification and Accreditation (C&A): Security certification is the process used to ensure controls which are
effectively implemented through established verification techniques and procedures, giving organization officials confidence that the appropriate safeguards and countermeasures are in place as means of protection. Accreditation is the provisioning of the necessary security authorization by a senior organization official to process, store, or transmit information. Risk Adjustments: Contingency plans and exceptions should be generated so that the residual risk be above the acceptable threshold.

Cisco 210-060 dumps has set various aims and responsibilities for qualifying applicants. “Implementing Cisco Collaboration Devices v1.0”, also known as 210-060 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 210-060 dumps exam questions answers are updated (203 Q&As) are verified by experts. The associated certifications of 210-060 dumps is CCNA Collaboration. Every responsibility carries some significant objective, for that reason the recruiter and examiner has designed some exam based topic which directly relates to their purpose. Cisco https://www.pass4itsure.com/210-060.html dumps Cisco Certified Network Associate Collaboration has been intended to authenticate the credentials of. And their major targeted audience for the exam is Assistant Support Engineer.
