Released the latest ISC CISSP exam dumps! You can get CISSP VCE dumps and CISSP PDF dumps from Pass4itsure, (including the latest CISSP exam questions), which will ensure that your CISSP exam is 100% passed! Pass4itsure CISSP dumps VCE and PDF — https://www.pass4itsure.com/cissp.html Updated!
Know what CISSP is
CISSP stands for Certified Information System Security Expert, and it is a certification created by the International Information System Security Certification Consortium (ISC) 2 in 1991. CISSP certification is a way to show your knowledge and prove your expertise. You can establish and lead an information security plan.
You have to pass the exam itself, a 6-hour, 250-question, 8-domain Goliath. The minimum passing score is 70%.
Multiple learning resources (free) for CISSP exam study guide – Pass4itsure

ISC CISSP study guide pdf free download
[free pdf] CISSP exam dumps pdf https://drive.google.com/file/d/1h5EX_Mn-AklTeSInmGEkFZsMNSVNtwM8/view?usp=sharing
ISC CISSP exam video learning (YouTube)
Link: https://youtu.be/HiPeJwS8qBw
ISC Certification CISSP practice tests online
QUESTION 1
What Is the FIRST step in establishing an information security program?
A. Establish an information security policy.
B. Identify factors affecting information security.
C. Establish baseline security controls.
D. Identify critical security infrastructure.
Correct Answer: A
QUESTION 2
Intellectual property rights are PRIMARY concerned with which of the following?
A. Owner\\’s ability to realize financial gain
B. Owner\\’s ability to maintain copyright
C. Right of the owner to enjoy their creation
D. Right of the owner to control delivery method
Correct Answer: D
QUESTION 3
Which of the following is a characteristic of the initialization vector when using Data Encryption Standard (DES)?
A. It must be known to both sender and receiver.
B. It can be transmitted in the clear as a random number.
C. It must be retained until the last block is transmitted.
D. It can be used to encrypt and decrypt information.
Correct Answer: B
QUESTION 4
The PRIMARY outcome of a certification process is that it provides documented
A. interconnected systems and their implemented security controls.
B. standards for security assessment, testing, and process evaluation.
C. system weakness for remediation.
D. security analyses needed to make a risk-based decision.
Correct Answer: D
QUESTION 5
Which area of embedded devices are most commonly attacked?
A. Application
B. Firmware
C. Protocol
D. Physical Interface
Correct Answer: A
QUESTION 6
An Intrusion Detection System (IDS) is generating alarms that a user account has over 100 failed login attempts per
minute. A sniffer is placed on the network, and a variety of passwords for that user are noted. Which of the following is
MOST likely occurring?
A. A dictionary attack
B. A Denial of Service (DoS) attack
C. A spoofing attack
D. A backdoor installation
Correct Answer: A
QUESTION 7
When using third-party software developers, which of the following is the MOST effective method of providing software
development Quality Assurance (QA)?
A. Retain intellectual property rights through contractual wording.
B. Perform overlapping code reviews by both parties.
C. Verify that the contractors attend development planning meetings.
D. Create a separate contractor development environment.
Correct Answer: B
QUESTION 8
[Miss the Question]
A. Verify the camera\\’s log for recent logins outside of the Internet Technology (IT) department.
B. Verify the security and encryption protocol the camera uses.
C. Verify the security camera requires authentication to log into the management console.
D. Verify the most recent firmware version is installed on the camera.
Correct Answer: D
QUESTION 9
Which of the following BEST describes the responsibilities of a data owner?
A. Ensuring quality and validation through periodic audits for ongoing data integrity
B. Maintaining fundamental data availability, including data storage and archiving
C. Ensuring accessibility to appropriate users, maintaining appropriate levels of data security
D. Determining the impact the information has on the mission of the organization
Correct Answer: D
QUESTION 10
Which of the following MUST system and database administrators be aware of and apply when configuring systems
used for storing personal employee data?
A. Secondary use of the data by business users
B. The organization\\’s security policies and standards
C. The business purpose for which the data is to be used
D. The overall protection of corporate resources and data
Correct Answer: B
QUESTION 11
How does an organization verify that an information system\\’s current hardware and software match the standard
system configuration?
A. By reviewing the configuration after the system goes into production
B. By running vulnerability scanning tools on all devices in the environment
C. By comparing the actual configuration of the system against the baseline
D. By verifying all the approved security patches are implemented
Correct Answer: C
QUESTION 12
A company receives an email threat informing of an Imminent Distributed Denial of Service (DDoS) attack targeting its
web application, unless ransom is paid. Which of the following techniques BEST addresses that threat?
A. Deploying load balancers to distribute inbound traffic across multiple data centers
B. Set Up Web Application Firewalls (WAFs) to filter out malicious traffic
C. Implementing reverse web-proxies to validate each new inbound connection
D. Coordinate with and utilize capabilities within Internet Service Provider (ISP)
Correct Answer: D
QUESTION 13
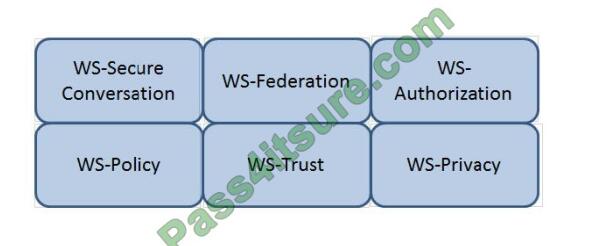
Which Web Services Security (WS-Security) specification handles the management of security tokens and the
underlying policies for granting access? Click on the correct specification in the image below.
Hot Area:

Correct Answer:
This kind of exam preparation is useful!
Pass4itsure Features

Pass4itsure discount code 2020
Please read the picture carefully to get 12% off!

P.S.
The above shared information about how to study for the CISSP exam to pass the exam preparation materials and recommended websites. Simple but effective exam preparation will ensure that you pass the exam quickly and successfully! Get advice and CISSP study guide from https://www.pass4itsure.com/cissp.html (Dumps Q&As: 970).
2020 Latest Pass4itsure CISSP Exam Dumps (PDF & VCE) Free Share: https://drive.google.com/file/d/1h5EX_Mn-AklTeSInmGEkFZsMNSVNtwM8/view?usp=sharing
