Released the latest EC-COUNCIL ECSAV10 exam dumps! You can get ECSAV10 VCE dumps and ECSAV10 PDF dumps from Pass4itsure, (including the latest ECSA V10 exam questions), which will ensure that your ECSAV10 exam is 100% passed! Pass4itsure ECSA V10 dumps VCE and PDF — https://www.pass4itsure.com/ecsav10.html Updated!
EC-COUNCIL ECSAV10 Exam Dumps
[100% free] EC-COUNCIL ecsa v10 pdf dumps https://drive.google.com/file/d/1rdNy3Z9bqxdI0vK2GQYdz4BiCpoEtAFJ/view?usp=sharing
Click here other exam dumps!
EC-COUNCIL ECSAV10 Practice Test 1-13
QUESTION 1
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in
an organization?
A. Vulnerabilities checklists
B. Configuration checklists
C. Action Plan
D. Testing Plan
Correct Answer: A
QUESTION 2
Tom is a networking manager in XYZ Inc. He and his team were assigned the task to store and update the confidential
files present on a remote server using Network File System (NFS) client-server application protocol. Since the files are
confidential, Tom was asked to perform this operation in a secured manner by limiting the access only to his team. As
per the instructions provided to him, to use NFS securely, he employed the process of limiting the superuser access
privileges only to his team by using authentication based on the team personnel identity.
Identify the method employed by Tom for securing access controls in NFS?
A. Root Squashing
B. nosuid
C. noexec
D. Suid
Correct Answer: B
QUESTION 3
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the
authentication procedures. Creating a backdoor is where an attacker obtains remote access to a computer on a
network.
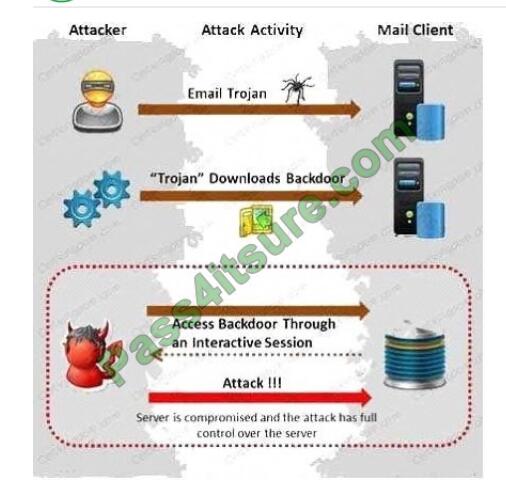
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a
target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine C. Sniffing to monitor all the
incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Correct Answer: D
QUESTION 4
Depp Networks is a leader in providing ethical hacking services. They were tasked to examine the strength of a client
network. After using a wide range of tests, they finally zeroed in on ICMP tunneling to bypass the firewall. What factor
makes ICMP tunneling appropriate to bypass the firewall?
A. Deep packet inspection
B. Firewalls can not inspect ICMP packets
C. Firewalls can not handle the fragmented packets
D. The payload portion is arbitrary and not examined by most firewalls
Correct Answer: D
QUESTION 5
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated
valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.
What are the two types of `white-box\\’ penetration testing?
A. Announced testing and blind testing
B. Blind testing and double blind testing
C. Blind testing and unannounced testing
D. Announced testing and unannounced testing
Correct Answer: D
QUESTION 6
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system
configuration and then scanning continuously without incorporating any information found at the time of scanning?

A. Service-based Assessment Solutions
B. Product-based Assessment Solutions
C. Tree-based Assessment
D. Inference-based Assessment
Correct Answer: C
QUESTION 7
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited.
Paulette\\’s duties include logging on to all the company\\’s network equipment to ensure IOS versions are up-to-date
and all
the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be
made. From the screenshot, what changes should the client company make? Exhibit:

A. The banner should not state “only authorized IT personnel may proceed”
B. Remove any identifying numbers, names, or version information
C. The banner should include the Cisco tech support contact information as well
D. The banner should have more detail on the version numbers for the network equipment
Correct Answer: B
QUESTION 8
A security analyst at Techsoft Solutions is performing penetration testing on the critical IT assets of the company. As
part of this process, he is simulating the methodologies and techniques of a real attacker because he is provided with
limited
or zero information about the company and its assets.
Identify the type of testing performed by the security analyst?
A. Announced testing
B. Blind testing
C. White-box testing
D. Unannounced testing
Correct Answer: B
QUESTION 9
StarMotel is a prominent chain of hotels in the world that uses high-tech solutions to ease the stay of their guests. In those high-tech solutions, they deployed RFID cards using which a guest can get access to the allocated hotel room.
Keeping an eye on the RFID technology and with an objective of exploiting it, John, a professional hacker, decided to
hack it in order to obtain access to any room in the target hotel. In this process, he first pulled an RFID keycard from the
trash of the target hotel and identified the master keycard code in several tries using an RFID card reading and writing
tool. Then, he created its clone using a new RFID card that gave him free reign to roam in any hotel room in the
building. Identify the RFID attack John has performed on the target hotel?
A. RFID spoofing attack
B. Reverse engineering attack
C. RFID replay attack
D. Power analysis attack
Correct Answer: B
QUESTION 10
Software firewalls work at which layer of the OSI model?
A. Data Link
B. Network
C. Transport
D. Application
Correct Answer: A
QUESTION 11
Identify the attack represented in the diagram below: A. Input Validation
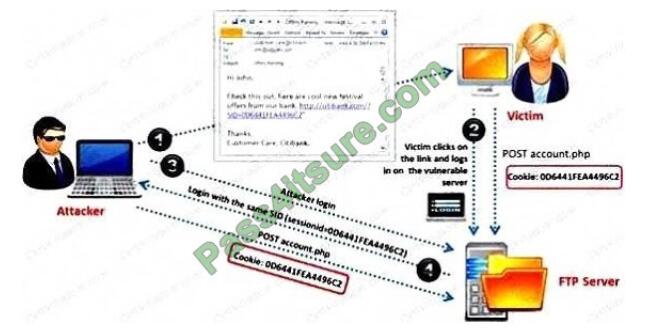
B. Session Hijacking
C. SQL Injection
D. Denial-of-Service
Correct Answer: B
QUESTION 12
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company\\’s
private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based
on the
specific needs of an organization.
Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic
weakness of which one of the following Protocol?
A. Lightweight Directory Access Protocol (LDAP)
B. Simple Network Management Protocol (SNMP)
C. Telnet
D. Secure Shell (SSH)
Correct Answer: D
QUESTION 13
SQL injection attack consists of insertion or “injection” of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application. A successful SQL injection attack can:
i) Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii) Execute administration operations on the database (such as shutdown the DBMS) iV) Recover the content of a given
file existing on the DBMS file system or write files into the file system v) Issue commands to the operating system
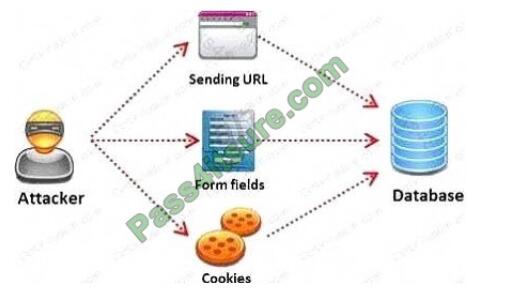
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields
whose values could be used in crafting a SQL query, including the hidden fields of POST requests, and then test them
separately, trying to interfere with the query and to generate an error. In which of the following tests is the source code
of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A. Automated Testing
B. Function Testing
C. Dynamic Testing
D. Static Testing
Correct Answer: D
Pass4itsure Discount Code 2020
Please read the picture carefully to get 12% off!

P.S.
Passing the EC-COUNCIL ECSAV10 exam is no more dream. Free share all the resources: Latest ECSA V10 practice questions, latest ECSA V10 pdf dumps, ECSA V10 exam video learning. Visit https://www.pass4itsure.com/ecsav10.html exam dumps with the latest questions.
